https://www.issa.org/Library/Journals/2008/October/Ben-Itzhak-Organized%20Cybercrime.pdf
By Yuval Ben-Itzhak
According Yuval (2008) cybercrime has developed into a fast-expanding, global industry. Its operations closely resemble the real business world, including profit-driven organized cybercrime. Cybercriminals use an arsenal of highly-effective crime tools, deploying sophisticated Criminal-2-Criminal (C2C) business models for their operations, heavily borrowing and copying from the legitimate business world. These kinds of crime pros also use robust and scalable crimeware that gives them maximum flexibility in terms of command and control for stealing and trading data. Cybercrime attacks are made easy due to the availability of crimeware toolkits. These toolkits are “how to…” software packages that instruct users step-by-step how to infect a system, followed by how to retrieve data for financial gain. Crimeware toolkit creators also deploy Crimeware-as-a- Service (CaaS). A classic example is the notorious NeoSploit toolkit that contained a delivery system for the Trojan upon a successful exploitation.
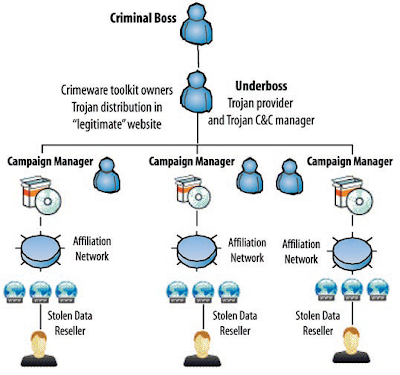
The damage for both organizations and individuals resulting from successful crimeware attacks is widespread and long-lasting – no organization, company, enterprise or business with Internet access is safe. This vision is confirmed by Marcus Alldrick, responsible for information protection and continuity at Lloyd’s. He pointed out that targeted attacks perpetrated by organized crime are on the increase due to the high return on investment. Fighting cybercrime is problematic in many aspects. In contrast to classic crimes such as drug offences or fraud, cybercrime has a vast scope, consisting of all kinds of actions designed to steal data for profit. Location is a problem as well; crimeware servers are often in a different country than the criminals that operate them.
By SITI FARAH LINA BT ABDUL RAHIM
2008285658
MC22S5A